CYBER 2 CAR
Preventing attacks from reaching the Connected Car
Whereas other companies focus on blocking cyber-attacks after they have reached the car
CYBER 2 CAR
Preventing attacks from reaching the Connected Car
Whereas other companies focus on blocking cyber-attacks after they have reached the car
THE PROBLEM
THE PROBLEM
- Hackers can remotely compromise the car systems
- Car data can be faked – causing incorrect or unnecessary treatment
- Autonomous cars can be hijacked
- Connected cars can be forced into an accident
- There is no prevention after the attack has reached the car
THE SOLUTION
- Cyber2Car prevents attacks from reaching the Connected Car
- No need to change the software of the car
- Does not require any updates
OUR DISRUPTIVE TECHNOLOGY



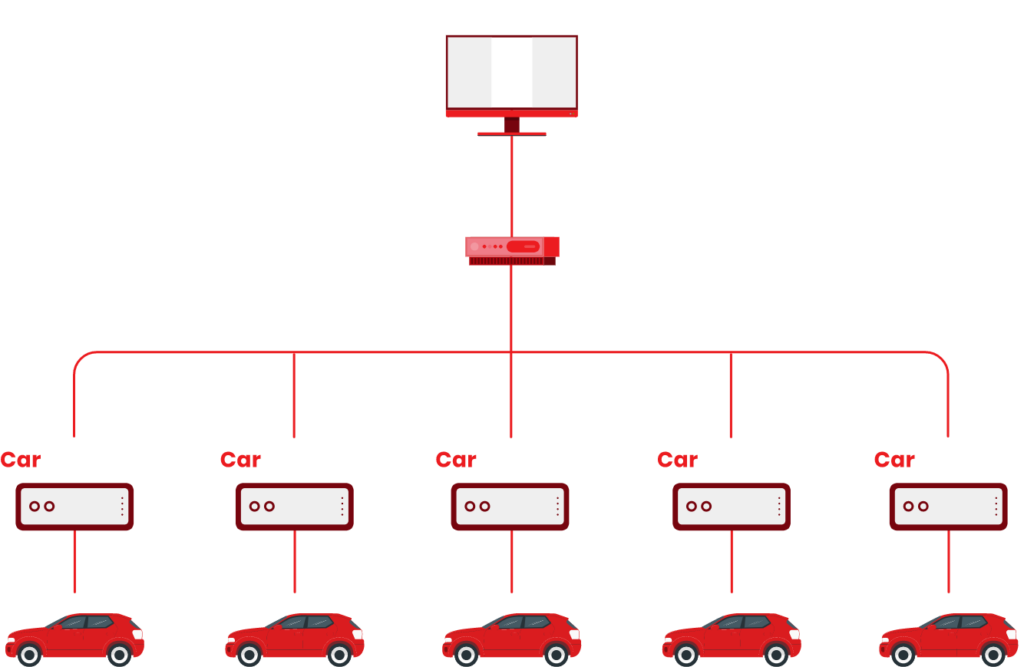
PREVENTION OF ATTACKS FROM REACHING THE CONNECTED CARS
- Total prevention with no detection
- Based on mathematical chaos
- The system cannot be breached
- Anomaly Detection is not required
- Intrusion Detection is not required
- Behaviour Analysis is not required
HACKER CHALLENGES
0
SATISFIED CUSTOMERS
0
Many
PATENTS
0
PROVEN
TECHNOLOGY
PROVEN
TECHNOLOGY
SATISFIED CUSTOMERS
0
Many
HACKER CHALLENGES
0
PATENTS
0
SEAL OF EXCELLENCE

CONCLUSION
GROWING MARKET-
BIG POTENTIAL
DISRUPTIVE
TECHNOLOGY
(based on the proven Cyber2OT technology)
TEAM OF WINNERS
PREVENTING ATTACKS
FROM REACHING THE CONNECTED CARS
(The only system in the world)
NETWORK DESIGN