THE BENEFITS OF THE
CYBER 2.0'S SOC
Security Operation Center
THE BENEFITS OF THE
CYBER 2.0'S SOC
CENTRAL CONTROL AND MANAGEMENT
REAL-TIME INFORMATION ABOUT WHO WAS ATTACKED AND WHAT IS THE SOURCE OF THE ATTACK
COMPLETE PREVENTION OF INFRASTRUCTURE (OT) ATTACKS USING CYBER 2.0 GATEWAY DEVICES
IMMEDIATE PREVENTION OF REMOTE ACCESS OF ATTACKERS TO OTHER BODIES, WHO HAVE NOT YET BEEN ATTACKED
TRANSFER (AT THE CLICK OF A BUTTON) ALL ENTITIES, INCLUDING THEIR COMPUTERS AND SYSTEMS, FROM MONITORING MODE TO PROTECTION MODE
HOW THE CYBER 2.0 SOC SYSTEM WORKS
- Central monitoring of all bodies in one central location
- Creating an inventory of all software and processes
- Analysis and learning of retinal behavior, for the purpose of providing smart alerts
- Investigation and forensics at the highest level
- Monitoring of existing software and processes on all computers
- Monitoring of all retinal movement that passes in and out of the components
- Analysis of active software and processes, in order to identify new processes
NETWORK DESIGN
DYNAMIC SYSTEM INVENTORY
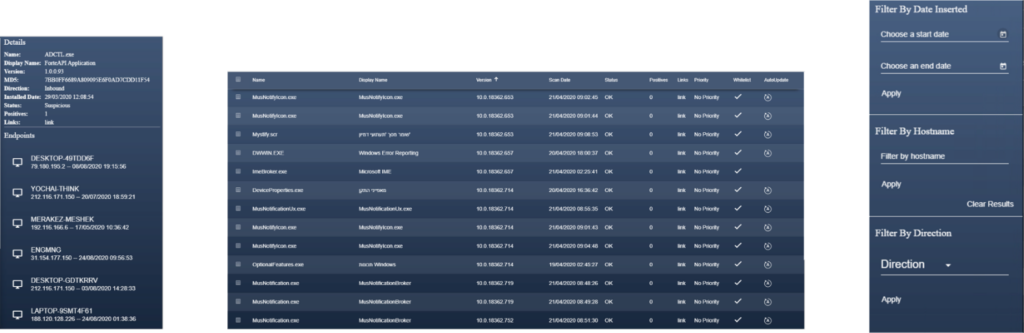
Display each software and each version of software, according to the computer on which they are installed
Create inventory of all the existing software and processes in monitored devices
Search in different sections, according to all the parameters collected in the monitoring
DYNAMIC SYSTEM INVENTORY
Display each software and each version of software, according to the computer on which they are installed
Create inventory of all the existing software and processes in monitored devices
Search in different sections, according to all the parameters collected in the monitoring
NETWORK TRAFFIC MONITORING
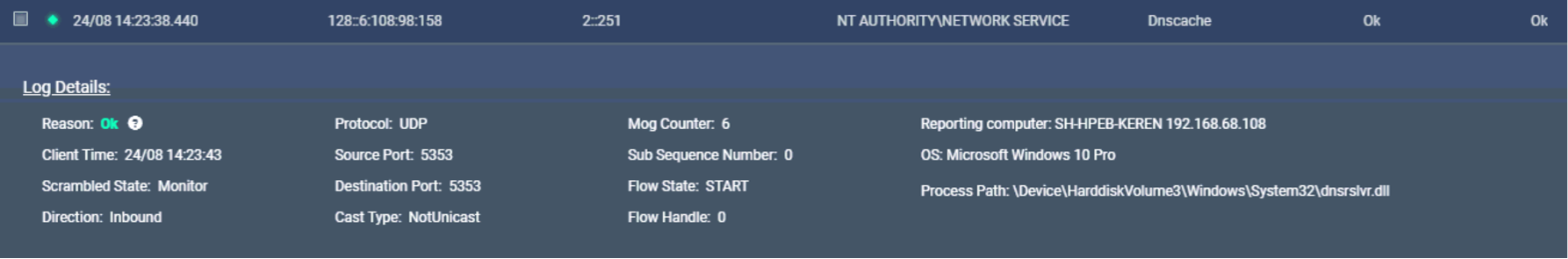
The information is stored in the form of FLOW, in the form of individual facts – which allows for efficient and fast reading of the information
The Cyber 2.0 system monitors all incoming and outgoing traffic from all components
