CYBER 2 OT
Preventing cyber-attacks from reaching the controllers and spreading through the network
THE PROBLEM
THE PROBLEM
- Today there is no defense against attacks in the OT field
- There is a fear of updates /changes in the controllers
- Regulating applies mainly to identify/detect
- The attacks in the OT field have a greater significance than in the IT field
THE SOLUTION
- The only system that provides prevention
- No need to install over the controller
- Easy to operate
- Works in unconnected networks
- Does not slow down the network
- Does not require any updates
OT/IOT ATTACKS
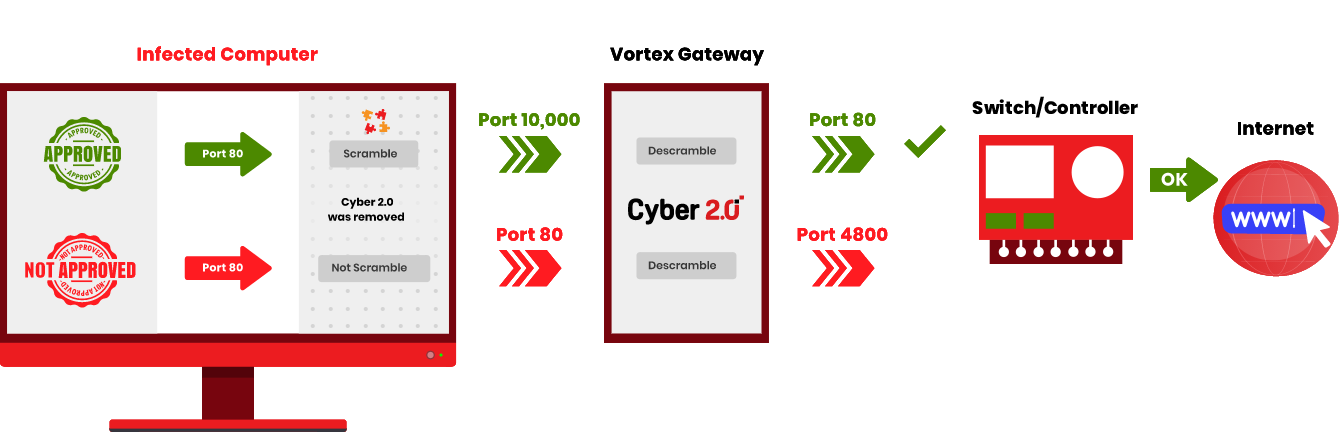
MARKING APPROVED PROGRAMS
THE IT MANAGER:
MARKS APPROVED PROGRAMS (1-2)
THAT ARE ALLOWED TO ACCESS THE NETWORK RESOURCES (THE PROGRAMS THAT OPERATES THE CONTROLLER)
NOT APPROVED PROGRAMS:
EVERY SOFTWARE THAT WAS NOT MARKED AS AN APPROVED PROGRAM (INCLUDING EVERY NEW AND UNKNOWN PROGRAM)
CHAOS ENGINE
FULL PROTECTION
In a closed vs a widespread environment
SINGLE GATEWAY
MULTIPLE GATEWAY
Cyber 2.0's solution to OT and Scada systems
We first developed the product for the IT world, and then expanded it to provide a complete solution to the OT world. We currently support a number of water systems in the State of Israel. Our system is installed in a number of factories in Israel and around the world, as well as in municipalities in Israel and the United States, in hospital chains in India, and more.
The advantage of Cyber 2.0 is that it is a single system, which protects the computers in the organization, and at the same time provides a complete solution for employees working from home (WFH), and also completely protects important facilities and infrastructure. As mentioned, the technology has been tested and proven and has achievements in its field.
The system operates in several modes according to the customer’s choice
Cyber 2.0 Modes
Explanation of the various modes and capabilities of the Cyber 2.0 system:
- Monitor
- Isolation
- Defense
Monitor Mode
Monitor Mode is the initial mode of the system when it is first installed on a network. It is designed to gather and analyze information about the network it is installed on.
Capabilities
- Creating a comprehensive inventory of every process or file that has been active since the system was installed and the information stored .
- It comprises:
- Files
- Versions
- Installed location
- Various other information
- Storing every network transaction on the installed system – the default setting is for 45 days (data can be stored indefinitely , depending on storage size)
- Analyzing every installed software, version or executable using the file Hash, and showing every known malicious software in your organization
- Allowing to create, edit and modify Cyber 2.0 Dynamic list
- Nothing will get blocked
- The customer will see what would or should have been blocked
Advantages
- Full view of the system
- A complete and comprehensive Inventory
- Full analysis of the network
Isolation Mode
Isolation Mode is designed to allow the organization to have fast and powerful protection against ransomware and similar forms of attack while keeping all the benefits of Monitor Mode.
Isolation Mode only prevents and blocks access to the file system. Any other protocol will not be blocked, only reported.
Capabilities
- All the benefits of monitor mode
- Example of Protected Protocols:
- UNC
- SMB
- Similar Network File System protocol
- Protects software from accessing the network file system
- Program with admin privileges will be blocked
- Access to map drive will be blocked
- Dynamic list automation is supported in Isolation Mode, allowing for smooth and almost zero maintenance
- No other protocol is blocked or affected
Advantages
- Full view of the system
- A complete and comprehensive inventory
- Fully analysis of the network
- Lightweight and easily manageable
- Powerful protection against the spread and effect of ransom virus and similar malicious software
Defense Mode
Internal Defense Mode is designed to bring the most cutting-edge defense into the organization. It creates an unappeasable chaos barrier between the computer of a specific network, and does not allow any unknown or unwanted application to traverse the network.
Any attempt by malicious software to bypass or deactivate the mechanism will lock the malicious software on the original computer, while the allowed programs work unhindered.
Capabilities
- All the benefits of Monitor Mode
- All the benefits of Isolation Mode
- All communication is scrambled
- All network traffic is subject to the dynamic list rules
- Dynamic list automation is supported in Defense Mode, allowing for smooth and almost zero maintenance
Advantages
- Full view of the system
- A complete and comprehensive Inventory
- Fully analysis of the network
- Light weight and easily manageable
- Powerful protection against the spread and effect of known and unknown malicious software