BLOCKING THE SPREAD OF ALL TYPES OF ATTACKS
BLOCKING THE SPREAD OF ALL TYPES OF ATTACKS
- ZERO TRUST: Not trusting anyone by default
- USUALLY, Zero Trust requires a lot of work in order to deploy and maintain it
- CYBER 2.0 requires zero amount of work
WE DON’T MISS ANY NEW ATTACK
- Mapping all active software (2000)
- Removing malicious (50)
- Blocking unknown (100)
- Approving (850)
- Blocking all the rest (3000-850)
(including every new software and virus, every 0-Day and every dormant software)
- IT manager gets the whole service from Cyber 2.0
WE CONTINUE PROTECTING
THE COMMON METHOD:
BLOCK out of the infected computer of any software that has been defined as malicious. The problem: the attackers who took over the computer will remove the cyber protection, and the software will exit.
OUR SOLUTION
Instead of trying to PREVENT, we ALLOW Malware to go out of the infected computer.
Because this malware is not blocked when it goes out, it will be blocked on the receiving computers. So, we continue protecting the organization even if Cyber 2.0 is removed from the infected computer.
OUR PREVENTION
ALL ADVANCED ATTACKS AGAINST CYBER 2.0 WILL FAIL
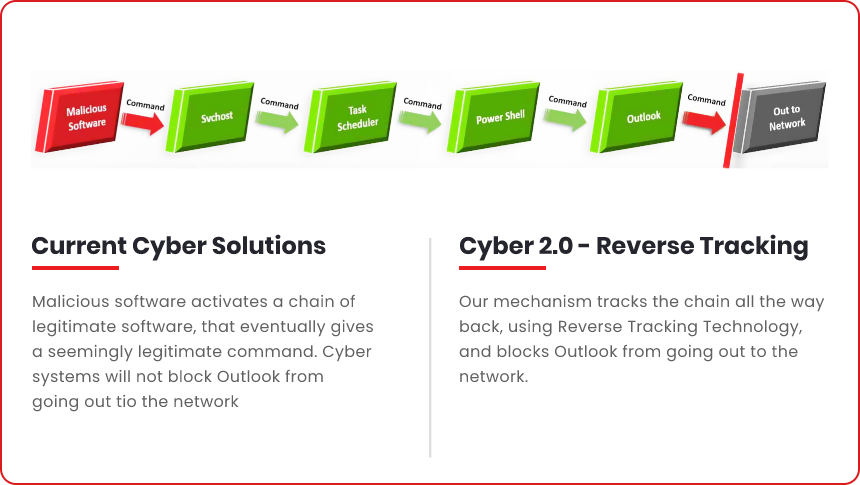
BYPASSING CYBER 2.0 WILL FAIL
Not approved software will still go out with the original port
DEACTIVATING CYBER 2.0 WILL FAIL
All software will go out with the original port
ADDING SOFTWARE TO THE LIST WILL FAIL
The system will allocate incorrect ports
MALICIOUS SOFTWARE USING OTHER SOFTWARE WILL FAIL
THE REVERSE TRACKING MECHANISM
- Every process and every library file that loads is recorded
- The system takes their MD5 and SHA signature
- Every access of a process to another process is recorded
MATHEMATICAL CHAOS MODEL
VS.
BIOLOGICAL MODEL
THE CYBER WORLD
is based on
biological models
that are vulnerable to attacks
by systems using similar models (hence where the terminology virus and anti-virus comes from)
is based on
mathematical chaos model
that cannot be breached
EXPLAINING CHAOS THEORY
Vortex Gateway FOR FIREWALL / CONTROLLER / CAR
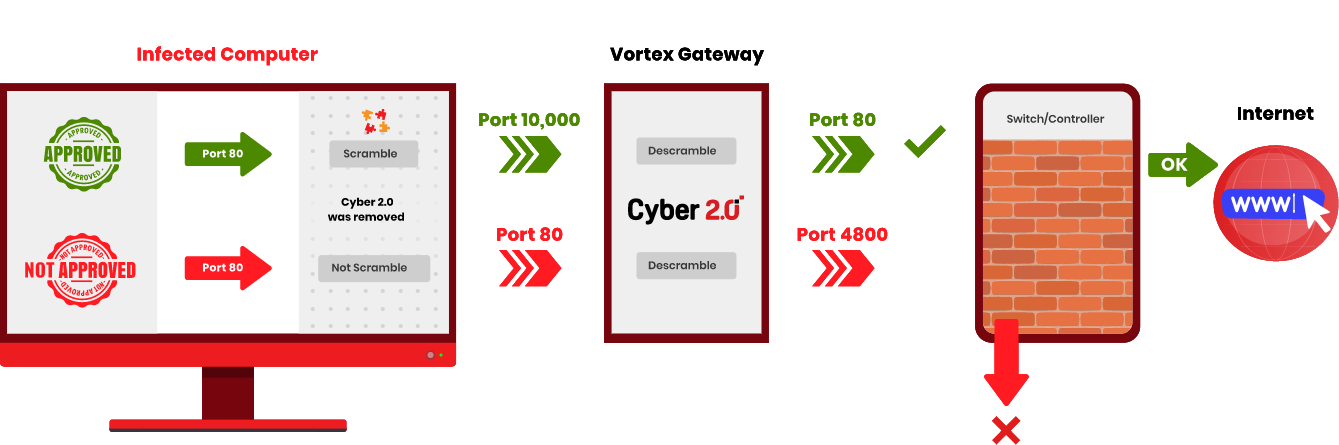
SIMPLE INSTALLATION
AN AGENT WILL BE INSTALLED AT ANY ENDPOINT, CONNECTED TO A CLOUD SERVICE OR AN INTERNAL SERVER

STARTING WITH MONITOR MODE, AND LATER MOVING TO DEFENSE MODE
CYBER 2.0 INTERFACES WITH YOUR SYSTEMS, WITHOUT THE NEED FOR ANY ADDITIONS OR MODIFICATIONS

THE PATENTS
Unique Scrambling System- chaos engine
(approved US 9,838,368, US 10,313,318)
Unique Server Support System
(approved US 9,794,277, US 9,985,981, US 10,333,956)
Reverse Tracking Technology System
(approved US 10,616,231)
Creating multiple Plans without the use of hardware
(approved US 10,397,196)
Unique Gateway System
(submitted)
Reverse Chaos for employees who work at home
(submitted)
Rendering Reverse Engineering ineffective
(in process)
Automatic creation of dynamic lists
(in process)
Chaos SSL
(in process)
OUR SYSTEM ON-PREMISE
SYSTEM CAPABILITIES
- Provides a complete EDR (Endpoint Detect & Response) solution, and beyond
- Provides a complete MDR (Manage Detect & Response) solution including SOC
- Provides a complete NDR (Network Detect & Response) solution including Network Obscurement
- Provides a complete XDR solution (Extended Detect & Response) which is an extension to Device Control
- Provides one complete solution for both IT systems and OT and Scada networks
- Operates in several modes (Monitor, Isolation and Full Defense)
- Provides Network Access Control (NAC)
- Based on the principle of ZERO TRUST
- Has FORENSIC CAPABILITIES
- Provides a complete solution for employees from home (WFH)
- Provides a continuous and ongoing Risk Assessment for the organization
- Its installation can be on premise or in the cloud
- The process of installing it is simple and easy
COMPETITIVE LANDSCAPE
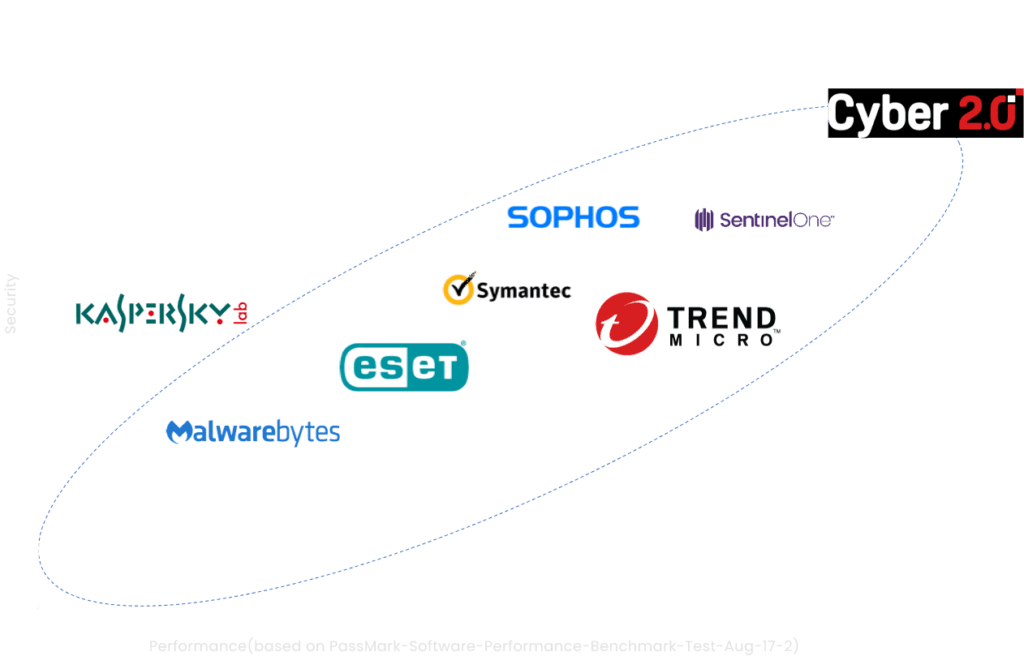
THE PERFORMANCE IS BASED ON:
CPU usage, Memory Usage, Network throughput, Boot Time, Browse Time and File Usage (copy, move, delete, Write, open and close).
FAQ
Frequently Asked Questions
Cyber 2.0 is a new, revolutionary and game-changing system unlike any other. This is an innovative EDR system that combines Zero-Trust and Network-Obscurement solutions, and a breakthrough technology based on the Mathematical Chaos model.
Definitely yes. Once the system is deployed in protection mode, only authorized devices will be able communicate with each other. Any attempt to contact using unauthorized or unknown devices will encounter a wall of chaos.
Definitely yes. When system agents are installed on home employees’ computers, they prevent malware from leaking into the corporate network. Other systems deal mainly with permissions – that is, which of the employees is allowed to call the organization from home. But if the computer at home of a licensed employee has been attacked, the permissions system will not prevent the attack from leaking into the organization. The Cyber 2.0 system, however, will prevent the spread of such an attack.
Cyber 2.0 system implements the principle of Zero-Trust, which is uniquely implemented to allow for easy control of the information that passes through the corporate network.
The system generates the first risk report within 14 days, after which the system issues these reports on demand or on a regular basis.
Absolutely yes. The system stores all network information in the form of flow. This allows tracking of all network traffic generated in the organization in a simple and efficient manner.
These attacks are automatically blocked by Cyber 2.0 System.
The command will run, but Cyber 2.0 System will block the access of the legitimate software, and will not allow it to go out of the computer or receive new commands. The administrator will receive an immediate alert.
Cyber 2.0 System renders IDS and IPS systems virtually obsolete. However, the organization may use them to monitor illegitimate traffic (unscrambled by Cyber 2.0) or allow the Cyber 2.0 Gateway system to translate the communications.
The systems on the market are usually based on learning the organization’s routine, and then alerting Anomaly Detection or trying to block software that has been found to be malicious. The problems in these systems are:
- An organization’s routine is not a regular thing. There is a daily, weekly, monthly, quarterly and annual routine.
- Once such cyber software has studied the organization – it tries to detect new anomalies. However, any malware that was installed before receives permission and is registered on the organization’s list of approved software.
- Not every routine anomaly is a malware or attempted attack, so there are a lot of false positives.
- At any given moment new malware appears, and most of them will not be detected by these systems.
Cyber 2.0 software does not perform Detection in this way. The system initially defines and marks only those programs that are allowed to move across the network and make use of network resources (about 100 programs out of thousands of programs that exist in the organization’s computers). For example: Office software is allowed to be used. A screensaver must not move across the network and use network resources. Photoshop software – for a certain organization that has not purchased it, is not allowed to move, but for a second organization it is allowed, and a third organization will want to give permission only to a number of computers to use it. Software that has not been authorized to roam the network – including any new and unfamiliar software, whether malicious or not, (and any new virus) will be blocked by Cyber 2.0 . In addition, the reverse threading system allows our system to check every process that is loaded on the computer and verify by MD5 by size and by SHA whether the file is authentic or not, and whether it is approved to move around the network.
- First, in other systems, if the detection system fails completely to detect new software, the prevention systems will not even try to block it
- Even if they detect it during the detection phase, once the attackers have taken over the infected computer, they will remove all the cyber software that protects the computer. Therefore, there will be no one to protect and prevent the exit of the same malware from the computer into the corporate network.
The attack will enable the command to run, but Cyber 2.0 System will block the access of the legitimate software, and will not allow it to go out of the computer or receive new commands or instructions. The administrator will receive an immediate alert.
All supported operating systems work on all virtual platforms.
Cyber 2.0 works seamlessly with network segmentation.
Many White List based systems have failed for the following reasons:
- The IT manager is required to register all the legitimate software in the organization, and he does not have the knowledge and ability to do so (some of the software was installed by his predecessor in office, some by users, some by other software and more)
- Managing the list requires daily routine maintenance
- In many cases, the attackers identify the system, attack, impersonate or overthrow it, and change the lists.
Cyber 2.0’s White List is different:
- Cyber 2.0’s unique patent is not based on the standard White-List, but on an automatically built Dynamic-List.
- It relates only to software that go beyond the confines of the computer, moves across the network organization, and uses network resources (the rest of the software is irrelevant).
- It is built so that any change or addition to the list, will lock the traffic from the computer out.
- It is built so that even if the system breaks down, the scrambling of the ports will stop, and no movement will be made from the infected computer.
The use of Cyber 2.0 renders standard-deployed internal Firewall obsolete. However, Cyber 2.0 System can work with, and even enhance their defenses.
Neither. Cyber 2.0 System is different from any current signature or algorithm-based system. Its internal logic is based on Mathematical Chaos model.
Since Cyber 2.0 is not a signature-based system, there is no need for regular updates. In the case of an agent update, the update is performed either from the cloud server or from the enterprise server.
In the MITM attack, an attacker intercepts the communication between the two legitimate devices and manipulates the exchanged information. Cyber 2.0 Chaos engine scramble the ports and changes the scrambling tables in both the scrambling source and destination ports between protected computers every second.
Scrambled network isolates protected computers from non-compliant network access, and thus the MITM attack will fail.
- Getting access to the targeted system using stolen or legitimate credential, That can be achieved by brute force or human engineering.
- After the first machine is infected, the malware starts scanning for vulnerability in its host and the surrounding network. Basically, it searches where it can access: shared folders, network drive and other shared resources. While scanning for vulnerability’s, the malware also collects user access, passwords, and other means to access the various resources.
- Infecting other machines, the malware uses the stolen credential to spread to other systems, and infect other computers. when reaching these other systems, the same methodology is used again – collecting credentials and spreading to other systems.
- While spreading inside the network the malware constantly creates a backdoor to its operators. In case of a successful removal by an antivirus, the operator can reinsert an improved version of the malware and restart the infection process.
- At this point the remote operator has full control over the infected network, they can encrypt it, steal information from it or do whatever they want with it.
When Cyber 2.0 is installed on the system, the following occurs: Cyber 2.0 interacts and blocks the malware scanning in phase 2. When the malware starts scanning the network for vulnerability, the Cyber 2.0 Chaos Mechanism prevents it from scanning the network causing any scan to retrieve the wrong results. Cyber 2.0 blocks the spreading of malware in phase 3.
- Getting access to the targeted system using stolen or legitimate credentials can be achieved by brute force or human engineering
- If the malware tries to spread using credentials stolen from the infected computer, the chaos engine once again interacts and blocks the spreading, even the computer had administrative credentials.
On the contrary. The total expense will be reduced because it will be possible to remove all the software that Cyber 2.0 shows are redundant, as some of our customers have already done. For example: IDS, IPS, Internal Firewall, Next Generation Anti-virus, NAC, BOYP, None Human DLP, Password-Acceleration, Honeypot, Send-Box as well as all systems based on behavior detection, anomalies, artificial intelligence and more.
Certainly not. The VORTEX does not function as a bridge, and does not require any change of settings in the network or the component that it is on. Moreover, the protected component does not “know” that it is protected since the connection to it is completely normal.
Our system supports organizations of all types and sizes, no matter how many end points they have.
The deployment process is designed to be easy and seamless. The client is a simple MSI installer, and can be deployed by any remote deployment system. Download Agent
No. You can deploy in sections as large or as small as you wish, and continue deployment whenever you decide. Cyber 2.0 can work with protected computers in defense mode, alongside computers in monitor mode and unprotected computers, all at the same time.
Viruses and Trojan programs disguised as legitimate programs (such as translation software, data compression software, accounting software and more), spyware masquerading as screensaver (Microsoft’s or others), browser hijacking and adware software (PUP and SPUP) that slow down computers, information and password stealing, malicious software, and unknown software running on the organization networks. Cyber 2.0 detects only active programs already in outgoing traffic.
Cyber 2.0’s SOC consists of senior information security analysts. It is active 24/7, and it allows us to:
- Centralized control and management of all end devices connected to our cloud.
- Receive real-time information about who was attacked and what the source of the attack was.
- Transfer (at the push of a button) all entities, including their computers and systems, (even those in monitoring mode) to protection mode.
- Prevent immediately remote access of attackers to other bodies that have not yet been attacked.
- Absolute prevention of OT infrastructure attacks) using Cyber 2.0 gateway devices.