The Technology – IT
Zero Trust
Reverse Tracking
Zero Day
Prevention
Detection

The Chaos Model
Other cybersecurity systems
is based on
biological models
that are vulnerable to attacks
by systems using similar models
(hence where the terminology virus
and anti-virus scomes from)
Cyber 2.0 has registered 9 patents

We Solve Two Fundamental Cybersecurity Problems
Problem 1 - Detection

No cyber company can identify
every new attack
( Zero-Day )
Using AI > creates thousands of mutations >
impossible to detect all of them
We Solve Two Fundamental Cybersecurity Problems
The Cyber 2.0 Solution- Zero Trust

How we do:
The system does not need to detect each one of the new attacks
What we do:
We only define which software is allowed to move on the network
All others are automatically classified as unauthorized to move
including any new software (malicious or not) as well as any new mutation, especially those based on AI
We Solve Two Fundamental Cybersecurity Problems
Problem 2 - Prevention

Defense systems inherently can’t
block programs they failed to identify
Hackers Attack the first computer >Neutralize all defense
systems > Malware spreads to the organization
We Solve Two Fundamental Cybersecurity Problems
The Cyber 2.0 Solution- Mathematical Chaos

What we do:
Continues to protect the organization,
even if
the attackers have removed it from that computer
How we do:
Not allowed software exits from the computer freely
Allowed software does not get free passage
The blocking is done on the computers to which the malware was sent
Our Detection- Doesn't Miss Any New Attack
Maps all active applications
in the organization
Creates the list of applications that are
allowed to move on the network
Our Prevention - Continues Protecting
The technology: Chaos Algorithm
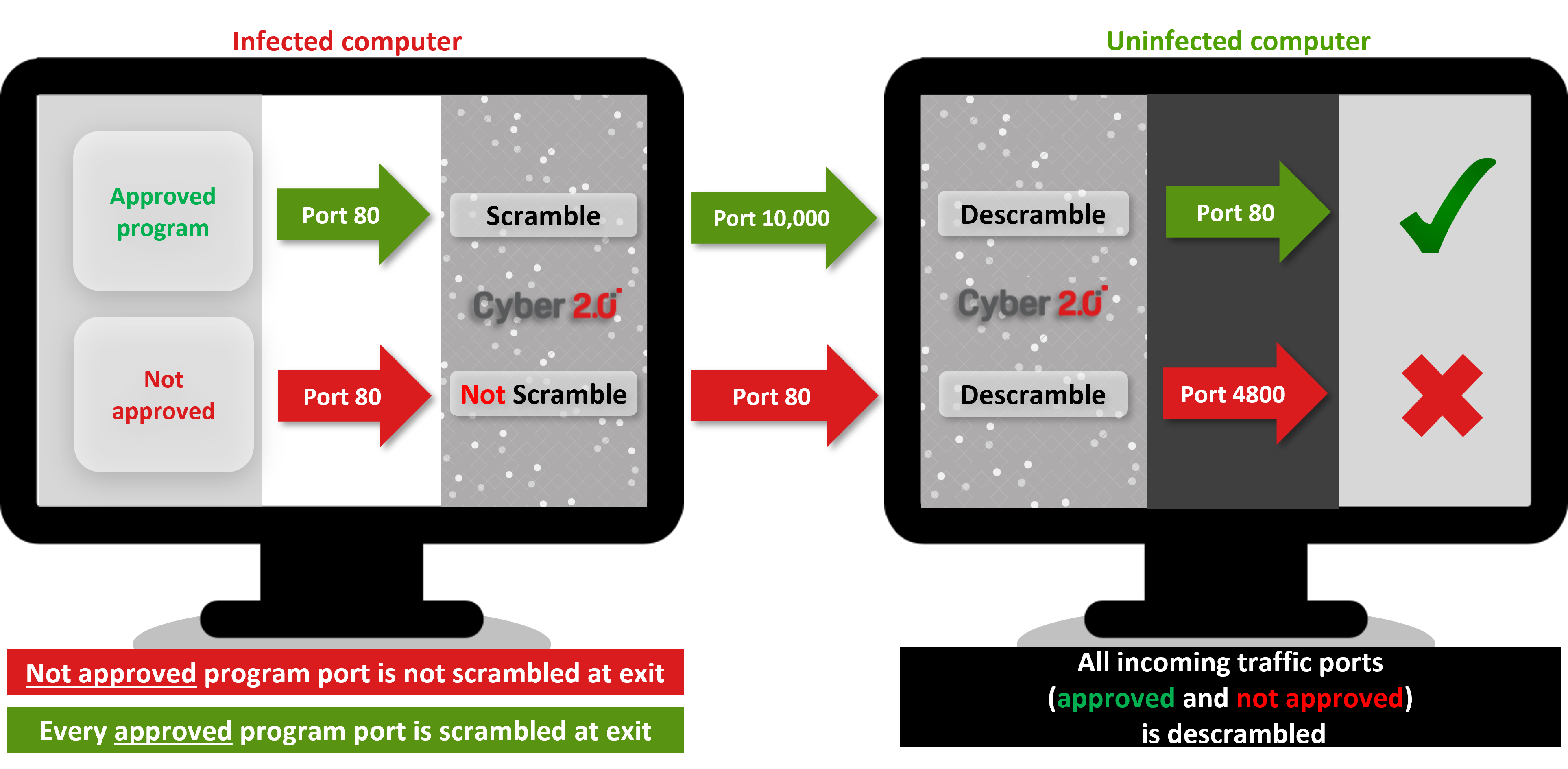
1. Bypassing Cyber 2.0 Will Fail
Not approved software will still go out with the original port number
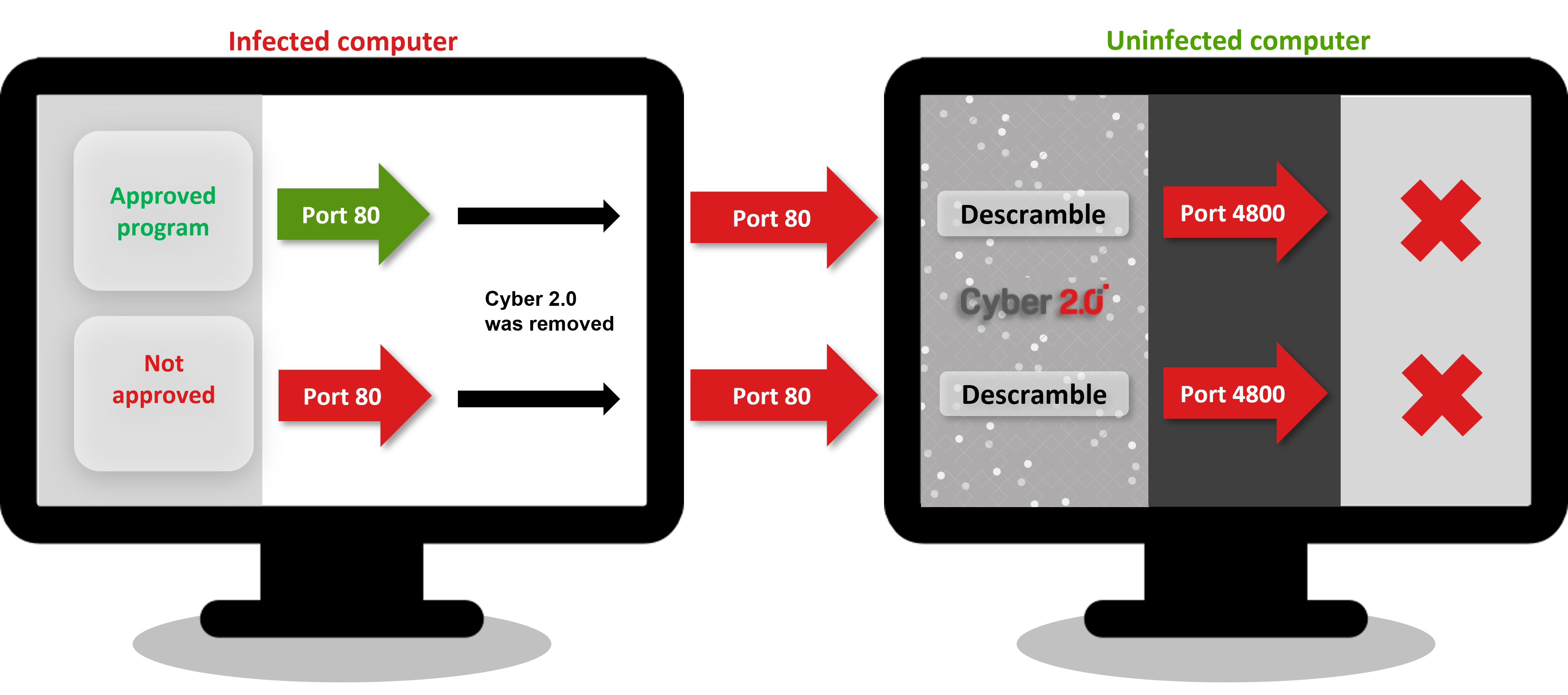
2. Deactivating Cyber 2.0 Will Fail
All software will go out with the original port number
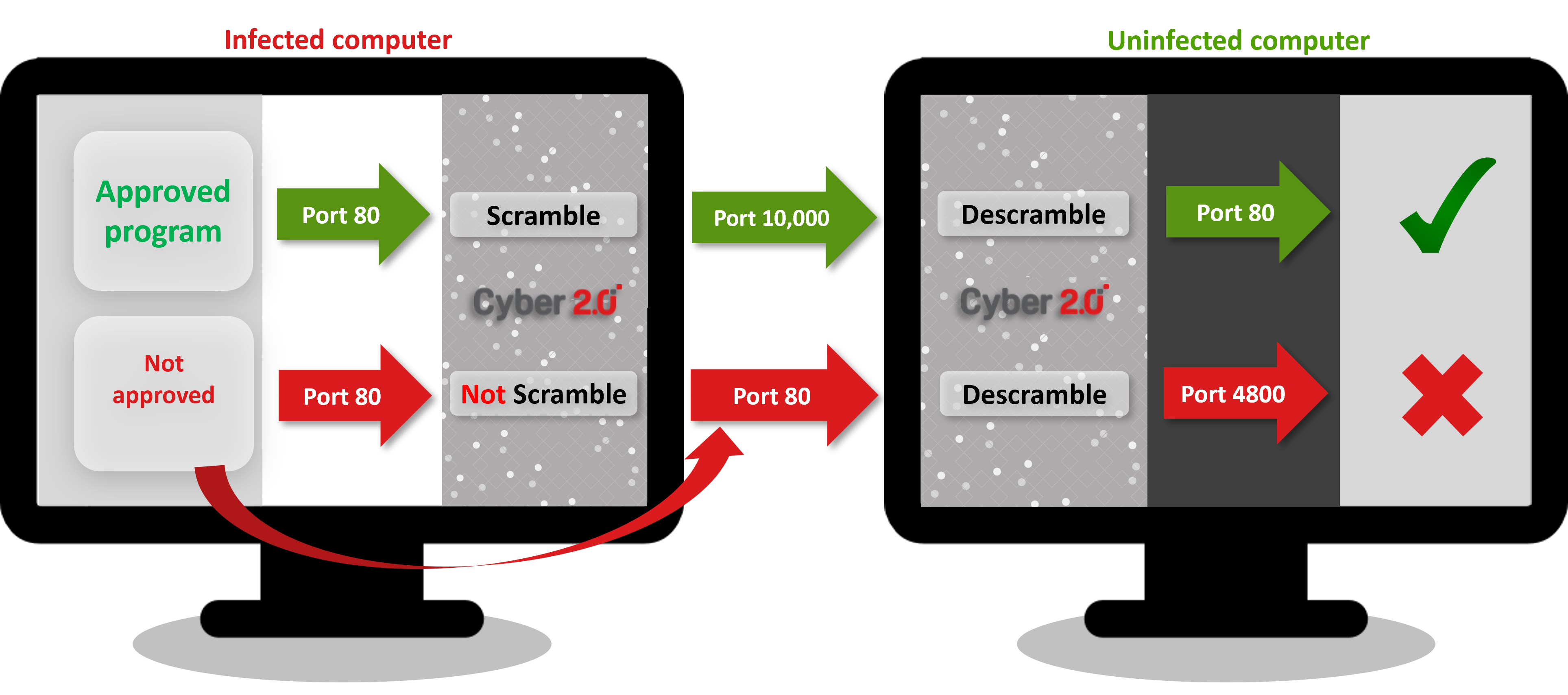
3. Adding Software to The List Will Fail
Not approved software will still go out with the original port number
and the system will allocate incorrect port number
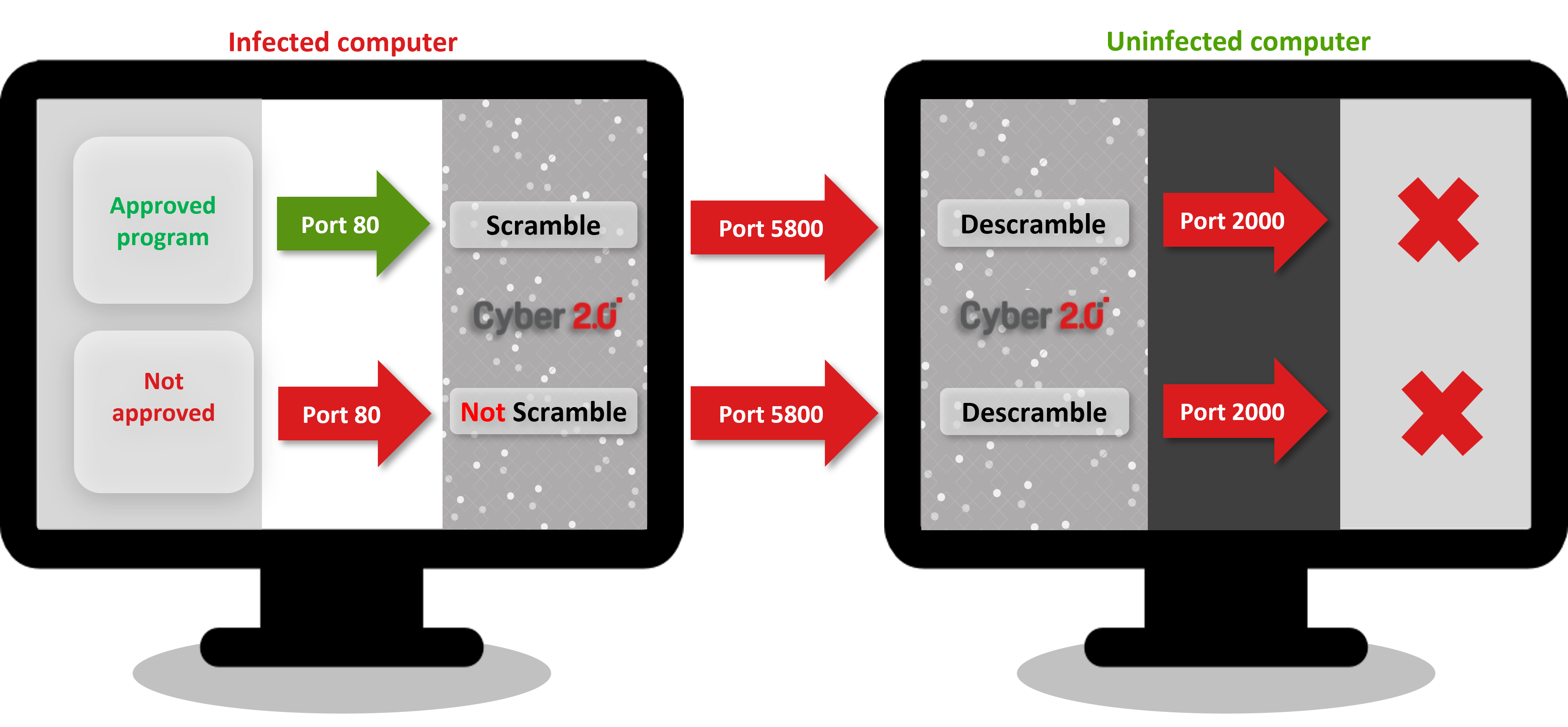
4. Malicious Software Using Other Software Will Fail
Outlook sends legitimate emails according
to legitimate commands
When hackers compromise Outlook, every cyber
defense company will detect it
But the hackers are sophisticated - they embed malware,
using other legitimate software
4. Malicious Software Using Other Software Will Fail
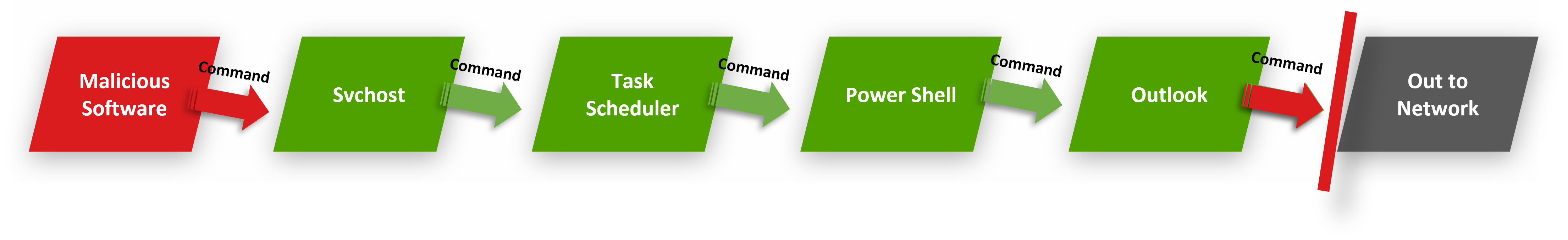
Other cybersecurity systems
Will not block Outlook from going out to the
network
Cyber 2.0 - Reverse tracking
Our Reverse Tracking Technology tracks the chain
all the way back and blocks Outlook from going out to
the network
Implementation process
POC - A very short Process that demonstrates the system’s ability:
Blocking the spread of attacks
Functioning with no interruptions, nor any load

Installation - Rapid deployment that is compatible
with all deployment methods (such as Sccm, Bigfix or GPO)

The Patents

|
Unique Scrambling System- chaos engine ( approved US 9,838,368, US 10,313,318) |

|
Unique Server Support System ( approved US 9,794,277, US 9,985,981, US 10,333,956) |

|
Reverse Tracking Technology System ( approved US 10,616,231) |

|
Creating multiple Vlans without the use of hardware ( approved US 10,397,196) |

|
Unique Gateway System (submitted) |

|
Reverse Chaos for employees who work at home (submitted) |

|
Rendering Reverse Engineering ineffective (in process) |

|
Automatic creation of dynamic lists (in process) |

|
Chaos SSL (in process) |
