The Cyber 2.0 Hackers Challenge
$100,000 prize to anyone who can bypass our protection
Anyone that manage to copy a single file from the protected fileserver.
We’ve invited hackers worldwide for years; Thousands have tried, none have succeeded.
How it works
- Goal: gain access and copy one specific file from the fileserver.
- Access: attackers connect over the Internet; no physical access required.
- Credentials: participants receive admin user & password for the computers and servers in scope.
- Protection: no firewall, no antivirus, no extra tools; the only defense is Cyber 2.0.
- Win condition: prove you copied the target file according to the event instructions (hash / timestamp verification).

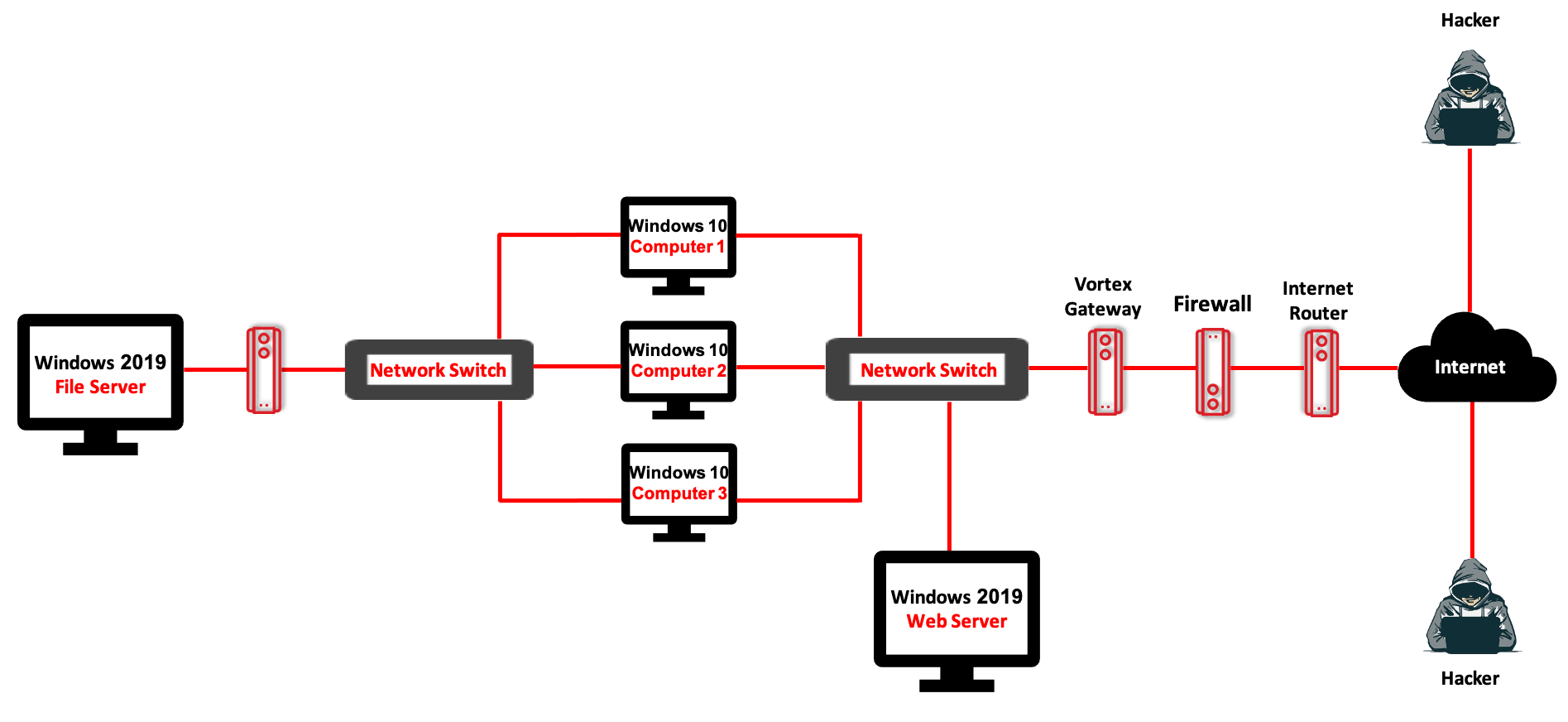
Network design (event setup)
The environment simulates the nightmare scenario for security teams: an attacker who already has administrative credentials and can move freely—unless Cyber 2.0 stops them at the receiver side.
- Endpoints & servers exposed for remote access (per event rules).
- A “crown-jewel” file placed on the fileserver as the objective.
- Receiver-side blocking enforced by Cyber 2.0 is the only control.
History & results
The challenge has run multiple years in Israel, Atlanta (GTRI), and online. Reports consistently show no one has successfully exfiltrated the protected file under the event conditions.
USA Challenge — GTRI (2019)
$100,000 prize offered; event coverage and recap.
European / 4th Challenge (2021)
Online edition; press & media mentions.
Earlier challenges (2018+)
Open network challenges; prize announcements.
FAQ
What exactly do participants receive?
Remote access plus administrative credentials to designated endpoints and servers in the challenge scope, as defined in the event brief.
Why is this different from a CTF?
The objective is singular and production-like: copy a real protected file, not solve riddles or collect flags. It tests whether spread can be prevented even when the attacker “has everything.”
What defenses are active?
No traditional controls (firewall/AV/EDR) are enabled; only the Cyber 2.0 receiver-side protection is running.
Think you can get the file?
Follow our announcements for the next edition of the Hackers Challenge.
